February 2016, was quite an exciting month for our emergency response code ninjas. There were several particularly savage attacks on a handful of sites that hadn’t been heeding the update signals from their WordPress admin page.
Introducing the Admedia Iframe Injection
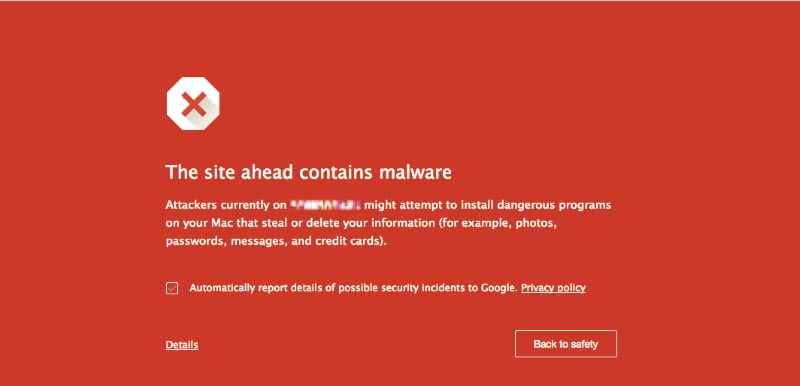
The first infection notices started to roll in globally around late January and early Feb 2016. We started receiving reports of the ‘Red Screen of Death’ from Google Chrome users.
This was a coordinated attack on a massive scale and fortunately, we only had a few instances to recover from. It should be noted that anyone who had been on top of their WordPress and Plugin updates had nothing to worry about.
What did it do?
This sneaky bit of code injected itself at the end of every available JavaScript file found linked in the code (every page has several).
Once installed the malware infected any first-time visitors to the website to which it would set a 24 Ad-Cookie. It would also inject an invisible iframe into the page. The iframe would randomly change between several pre-determined URL’s at each visit in an effort to serve its ads on the infected pages.
The visitor could get presented with a ‘fake’ Google Search page and would be attacked by malware after a search was made.
The malware also uploads several backdoor access points into various locations on the server while constantly updating the injected code. Hence, server admins are resorting to a complete ‘from scratch’ restoration of the web directory. Fortunately, all infections are at the disk level and did not affect the database content.
Additionally, the infection could cross pollinate other websites on the server for a real nasty ‘swarm’ effect. Fortunately, the instant we learned of this feature, our team locked down all of our web servers so that nothing could bounce between sites. It’s like a double deadbolt on your apartment door; someone could access the building but there’s no way they’re getting into your flat.
As mentioned, anyone currently engaged in a Caorda WordPress Maintenance program received immediate attention once the news broke of the exploit. We located and neutralized several sites that had been affected but hadn’t been flagged by Google as malicious. These clients saw no disruption in their operations. Sadly several other websites were left infected long enough for Google to notice and so flagged them as ‘Malicious’ in Chrome causing large disruptions in their online presence. Basically, when you are ‘flagged’ no one is going to visit your website until you resubmit your website to Google.
If you think a WordPress Security Program is something you might be interested in, please contact us at your leisure.
The Dreaded Fake WordPress Login Pages
Another infection that circulated around the same time was a particularly mischievous exploit that would create very sneaky backdoor pages which might appear to be part of the WordPress core. Pages like login.php or admin.php might seem like legitimate pages to unsuspecting site owners. However, they are there to allow malicious entry to the admin dashboard with full administrative access to your website.
What does it do?
What it does is entirely up to the attacker. With complete and total control over the website, the attacker will usually leave the other accounts in place so as not to raise an alarm. They would then build archived blog posts or add hidden links into established pages for search engine ranking purposes. These changes can often go unnoticed for months if carried out with stealth in mind.
In other scenarios, the attackers shut off access and take full control of the website. They would change all the passwords so the site owner is required to contact their hosting provider, and sometimes at great expense, hire a technician to reset their database passwords so they can access the site again. Often this is too late as the attackers have placed code throughout the site with no other option than to rebuild it from scratch. Again, at a direct cost to the owner.
Your brand can also take a hard hit depending on how long the site has been compromised and what sort of content or messaging the attacker places on the site. You can just use your imagination as to what could possibly be done; anything.
How can Caorda help?
Our clients that are subscribed to Caorda’s security program receive our constant attention. Using server monitoring applications, we watch for suspect activity and react accordingly. WordPress core files and plugin files are proactively updated as upgrades are released and not to mention the peace of mind that we’re looking out for you.
